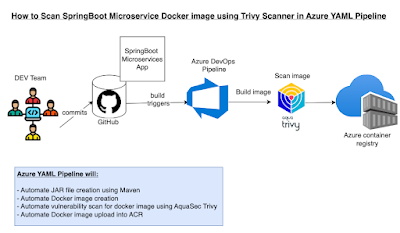
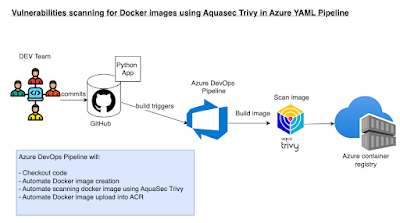
Checkov is a static code analysis tool designed to scan Infrastructure as Code (IaC) files and identify potential security and compliance misconfigurations.
Pre-requisites:
- Jenkins is Setup
- Terraform is installed in Jenkins
- Checkov is installed in Jenkins
- https://github.com/akannan1087/myInfra2021Repo
agent any
stages {
stage('Checkout') {
steps {
git 'https://github.com/akannan1087/myInfra2021Repo'
}
}
stage('Run Checkov Scan') {
steps {
sh 'checkov -d . -o junitxml > checkov-report.xml || true'
}
}
stage('Publish Report') {
steps {
junit 'checkov-report.xml'
}
}
}
post {
always {
archiveArtifacts artifacts: 'checkov-report.xml', fingerprint: true
}
}
}